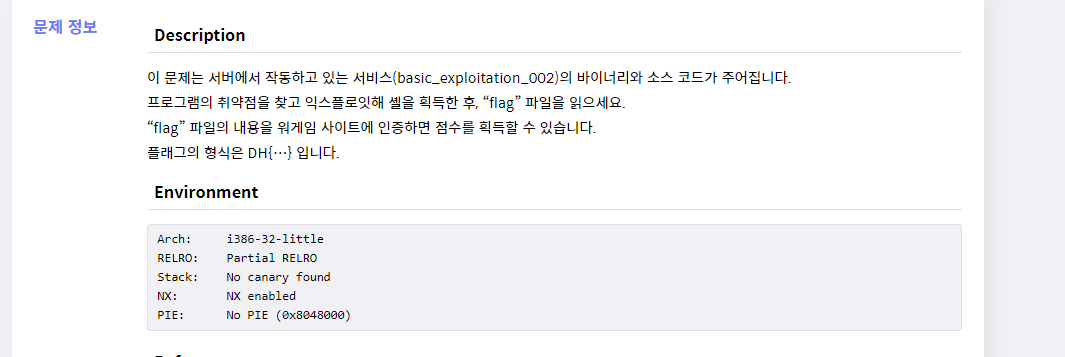
basic_exploitation_002

basic_exploitation_002
문제 풀이
또 x86..이네요 이거 이젠 익숙해지겠네 좋다
NX와 Partial RELRO.. 그러나 FSB로 풀어야하는 문제니까 C코드를 보시면

buf(0x80) 만큼 할당 read()에서 그만큼 입력받기에 BOF는 발생 X
그러나 printf(buf)로 FSB는 된다는 점과 get_shell() 함수를 이용하면 끝나는 점!
FSB : Format String Bug 로 개발자의 실수로 빛어진 버그

Exploit 설계
FSB는 %p %x %n %hn %N$FSB 등이 핵심으로써
스택은 쌓이기 때문에 아마 더 높은 변수에 존재할 가능성이 있죠 그럼 10보다 큰 값을 적당히 넣는다면
언젠간 name의 변수에 닿고 name에 "/bin/sh"를 입력하여 그 값을 넣는다면?
그럼 command와 name 사이의 거리만 구하면 exploit code가 작동되겠네요
그럼 바로 시작해볼까요?
Exploit
여러가지 방법이 존재하며 여기선 원시적인 방법은 제가 그전에도 실패한 경험이..
아래 코드를 보시면 원시적인 방식으로 할 수 있을 것입니다.
HackerSchool_level11
keyword : strcpy bof keyword : printf Format String keyword : NOP level11 - Write Up(NOP) 힌트가 코드네요... 위 코드를 보면 argv라는 main인자의 값을 받아서 출력하네요 setreuid가 있기에 level12로..
dystopia050119.tistory.com
저는 pwn에서 제공하는 fsb를 쉽게하는 fmtstr_payload를 사용할 것 입니다.
pwnlib.fmtstr — Format string bug exploitation tools — pwntools 4.8.0 documentation
A tuple (score, value, mask) where score equals the number of matching bytes between the returned value and target.
docs.pwntools.com
위에 링크에서 사용방법을 알려줍니다
fmtstr_payload(offset, writes)
* writes = {addr:value, addr2:value2}
이런 느낌입니다

그럼 저희는 bof가 발생이 불가하기에 main코드가 끝까지 실행되면 마무리되는
exit()에서 get_shell()까지의 길이를 알면 되겠군요
cs
코드.. 설명이랄게 없네요.. fmtstr_payload에 대하여 알아보았다?
pwntools가 정말 좋구나.. 라고 마무리 하겠습니다

참고 자료
참고 이미지